Network Solutions

Network Performance Management
Network performance refers to measures of service quality of a network as seen by the customer.

Network design, installation, and implementation
Network design refers to the planning of the implementation of a computer network infrastructure.

Switching & Routing
Switches are used to connect multiple devices on the same network within a building or campus. For example, a switch can connect your computers, printers and servers, creating a network of shared resources.
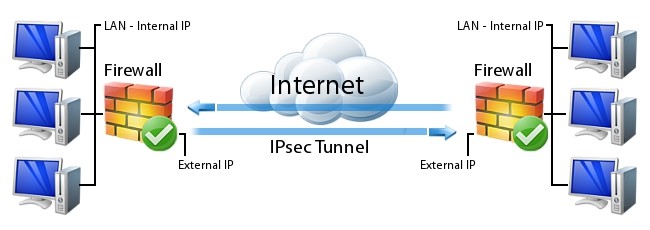
Gateway Firewalls / UTM
Data Loss Prevention (DLP) is the practice of detecting and preventing data breaches, exfiltration, or unwanted destruction of sensitive data.
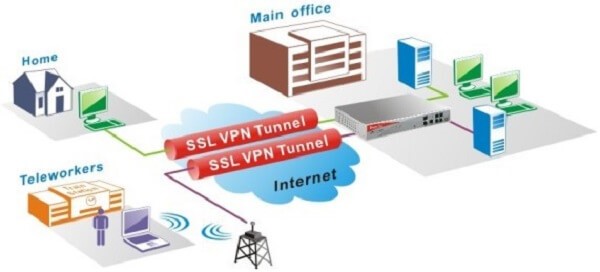
SSL VPN, IPSec VPN
A VPN provides a means by which remote computers communicate securely across a public WAN such as the Internet. A VPN connection can link two LANs (site-to-site VPN) or a remote dial-up user and a LAN.

Data leakage prevention, Email monitoring & control
Data Loss Prevention (DLP) is the practice of detecting and preventing data breaches, exfiltration, or unwanted destruction of sensitive data.
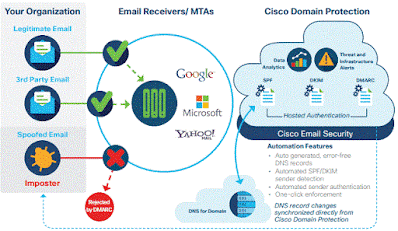
E-mail Security Solutions
Email security solutions are designed to protect against phishing attacks and other email-borne attack vectors, protecting email accounts from external threats.

VoIP, Video and Audio Conferencing
VoIP, Voice over Internet Protocol, allows you to make and receive telephone calls over the internet.

Domain & Mailing Solutions
the domain name example.com might translate to the physical address 198.102. 434.8. Other examples of domain names are google.com and wikipedia.org.
Network Security Measures Firewalling, Virus/SPAM protection, Control of the Internet usage
Network security measures are the tools and technologies such as firewalls and IPS.
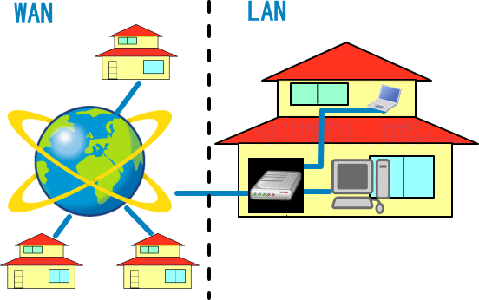
WAN/LAN/WLAN Implementation and configuration
A wide-area network (WAN) is the technology that connects your offices, data centers, cloud applications, and cloud storage together.
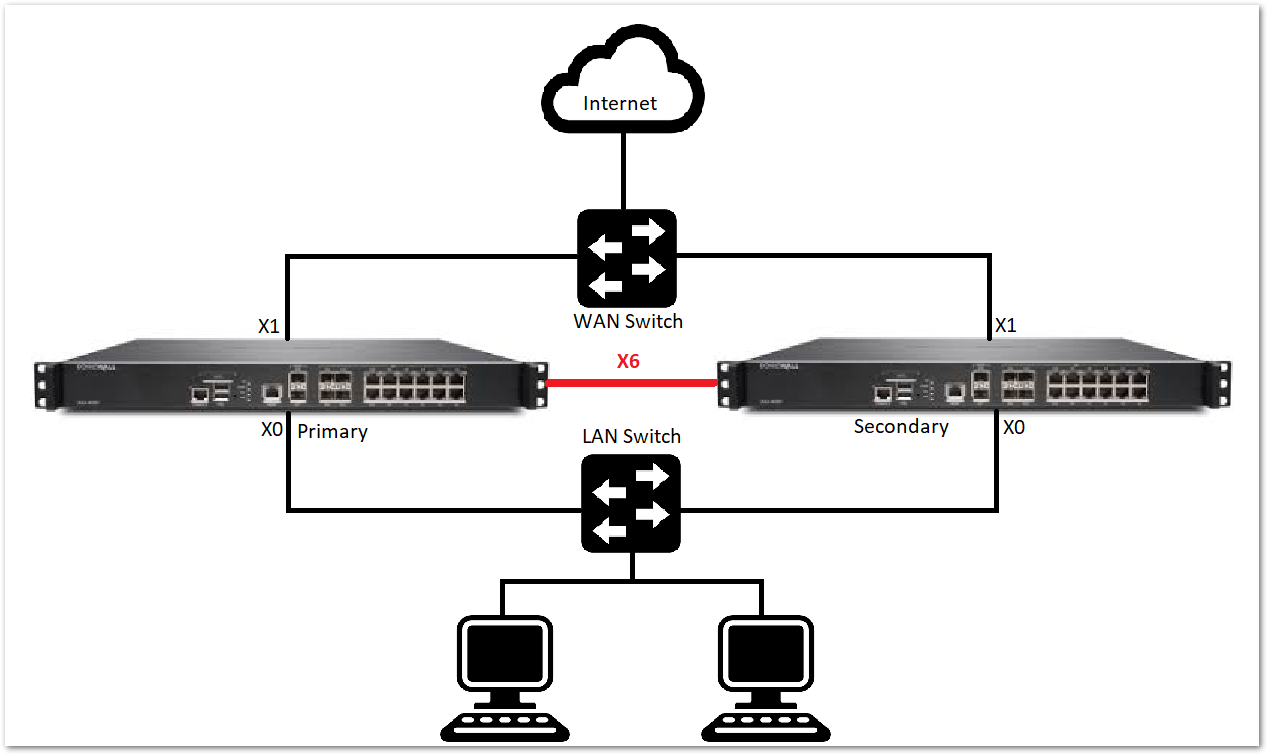
High Availability for Firewalls and servers
High availability (HA) is the elimination of single points of failure to enable applications to continue to operate even if one of the IT components it depends on, such as a server, fails.
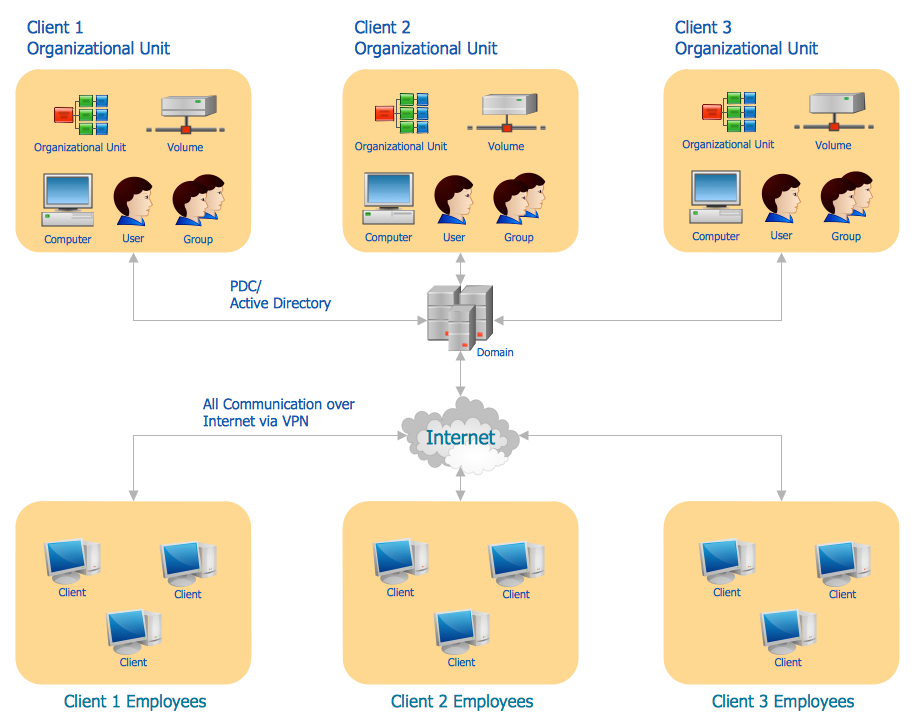
Configuring Active Directory Servers
Active Directory Domain Services (AD DS) is a server role in Active Directory that allows admins to manage and store information about resources from a network.
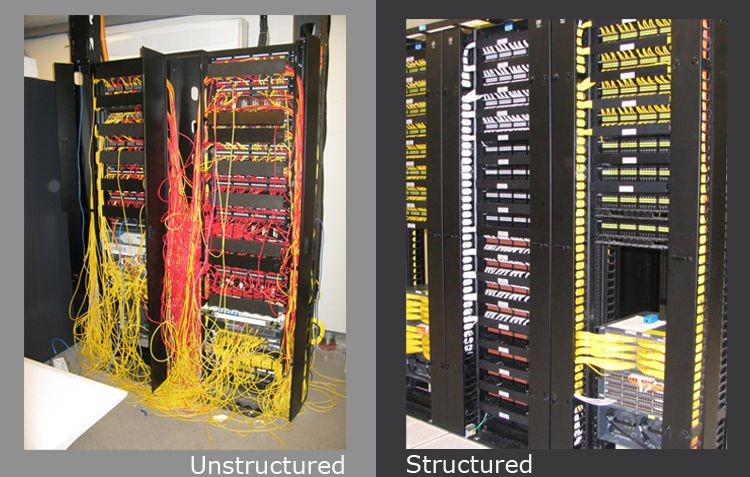
Structured Cabling Data & Voice
A structured cabling design provides a comprehensive infrastructure for businesses to transmit data, voice, alarm, video or signals through the network.
Storage & Backup Solutions
Check Out All Our Storage & Backup Solutions

Automated Backup
Automatic backup is a data backup model that enables users to back up their data with little to no manual intervention.

NAS/ SAN/ Unified data storage solutions
Overview. Network-attached storage (NAS) is a file-level storage architecture that makes stored data more accessible to networked devices.

Tape Backup (LTO)
Tape backup is the practice of periodically copying data from a primary storage device to a tape cartridge so the data can be recovered if there is a hard disk crash or failure.
Security Solutions
Check Out All Our Security Solutions

CCTV
CCTV is designed to help prevent and detect crime. It can reassure the public about community safety. It is located in public places to: provide evidence to relevant enforcement agencies.

Access Control
Access control is a security measure which is put in place to regulate the individuals that can view, use, or have access to a restricted environment.
